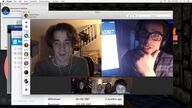
A useful independent subjective evaluation is not guaranteed. At the beginning of paragraph 4, you will encounter a large number of proper nouns, don't be afraid, you will have to learn it sooner or later.
First of all, this movie should not be classified as a horror movie, because the story is not absurd, disgusting, supernatural or supernatural, but I have to admit that using the first perspective to log on FB on the computer, video with girls, play online games with friends, Searching for hidden files, watching various hacker operations, watching videos of victims (especially from a surveillance perspective) and a series of audio and video have a strong sense of substitution, bringing a strong horror experience to the fear of the unknown;
Secondly, the film should not be classified as a science fiction film, which is the point I want to focus on talking with you.
I am an IT entrepreneur. Although I majored in material science, it did not stop me from following the development of IT technology. The reason why the audio-visual platform classifies it as a sci-fi film is nothing more than a variety of bizarre hacking techniques, including:
1. Intrusion of PC, router, mobile phone, monitoring equipment (terminal); 2. Hijacking of FB, Skype and other applications, 3. Video signal interference; 4. Geolocation tracking; 5. Data mining + face recognition + machine learning; 6 . Dark Internet; 7. Speech Recognition; 8. Internet of Things; 9. Blockchain; 10. Killing skills.
We have a premise: this is a movie . There is no need to worry about the protagonist's fucking NC, the plot is too extreme, unreasonable, the Internet police don't care, and so on, it's no coincidence that it's a book, and authenticity has never been the primary criterion for evaluating art.
What I want to say is that the first 9 items listed above are not future/unrealized things. On the contrary, the technical conditions are already in place. As for 10, I will not discuss it. I don’t know why the car in the ending is not. To be able to hit the shi male protagonist so accurately, it is quite difficult to reason convincingly. You should be more professional than me, so let's focus on the first 9 points.
The world we live in now is full of cameras (terminal devices), especially in big cities in China, it is best not to commit crimes. If you do not commit crimes abroad, the probability of catching you within 72 hours is very high. The reason is that Tianyan . This involves IoT technology + data mining + face recognition + machine learning . What Sky Eye can do is not only to shoot, convert optical signals into electronic signals for storage, but to match the time, place, and image with your "identity" at the moment you are photographed. The terminal can handle many basic / Brainless computing, and determine whether to upload to the cloud, anyway, as long as the control center wants to call, you can always get sorted, clear and easy-to-use data. By the way, in the next few years you will see another term take off - edge computing, which is closely related to each of our lives. Data mining refers to the process of searching for information hidden in a large amount of data through algorithms, that is to say, making behavior judgments and predictions. (From Baidu Encyclopedia) Data mining is inseparable from machine learning. Machine learning is a multi-disciplinary interdisciplinary subject involving probability theory, statistics, approximation theory , convex analysis , algorithm complexity theory and other disciplines. It specializes in how computers simulate or realize human learning behaviors to acquire new knowledge or skills, and to reorganize existing knowledge structures to continuously improve their performance. (From Baidu Encyclopedia) At the same time, the combination of cloud computing, distributed processing technology, storage technology and perception technology completes the entire process from collection, processing, storage to forming results, which is often referred to as "big data". There is no privacy in the Internet era because all data can be obtained as long as it touches the Internet. In the era of big data, not only privacy cannot be absolutely protected, but many things that you can't even notice yourself can be analyzed by machines to predict your future behavior. This also laid a theoretical foundation for the various unconventional shots that appeared in the film.
Cooperate with hacking technology (this is not an independent discipline, but the reverse application of network security technology), as long as it is a network device, it is possible to be invaded , including your terminal equipment, mobile phone, computer, various Cameras, medical equipment, city brains, and Amazon cloud servers, carrier servers, mobile base stations, and even more NB-based applications such as FB and Skype can also invade the satellite central control, and positioning tracking is not a problem. Devices with a high level of security can only view data, while devices with a low level of security can be controlled, such as the camera's steering and focal length. After a router is hijacked, all information passing through the router can be read, written, or deleted, unless the information is encrypted before entering the router. The above actions all involve cryptography. Of course, encryption and decryption technology is a required course for hackers. Believe me, this subject is enough for a bachelor’s, master’s and doctoral degree, but there are already many common encryption and decryption tools. The blockchain mentioned in 9 also relies on asymmetric encryption to make Bitcoin. My zhihu has a question and answer about blockchain. You can go to zhihu and search for the user "Nanzheng" , and the signature is "somewhat interesting" , will not be described in detail here. The conventional abbreviation of Bitcoin is BTC, the XBT used in the film is that some people hope that Bitcoin can be accepted by the world and follow the ISO 4217 international standard to name it XBT. There are only four non-states in the world and no third-party organization is required. The supported currency units are Gold (XAU), Silver (XAG), Platinum (XPT), Palladium (XPD). And Bitcoin (XBT), as the fifth, of course, must comply with ISO standards.
There have been multiple video disturbances that are also worth mentioning. Some people may think that the hacker's clothes are coated with some material, which interferes optically. In fact, it is not so mysterious, and the cost is not so high. . You only need to interfere with the video signal. There are many methods, such as broadcast interference or high-frequency interference (this can only interfere with cables and antenna signals), power supply interference (after destroying the grounding, use the interference signal to superimpose the video signal or destroy the equipment in the device. The AC-DC conversion device pollutes the power supply, but these are traditional interference methods. Hackers are more likely to use their strengths instead of electrical and electrical engineering to tamper with algorithms and add interference sources during the conversion process after optical signal acquisition, which is equivalent to tampering with the image. The signal, the obtained photoelectric conversion signal or data can no longer be converted into the original image, the black is all black, and this task is no longer difficult. Therefore, although the terminal sees a fancy image, it does not mean that the lens is blurred. or the clothes are special equipment.
What's more sci-fi is that the chat room can't kick people, the font color and effect of the FB dialog box are different, and the message can be withdrawn. This may be hacked into the APP's database, or it may be hijacked by the router to let you see what you don't want to see. , but both need to be able to break through the security architecture of the APP , either from the cloud or from the terminal to dominate the data transfer of these accounts. To be honest, people who can do this are quite daunting. At least it is no problem to be a chief security architect in a leading Internet company.
As for the dark web , it is real, and it has not been around for three or five years. Unlike the Internet we use every day, the dark web is another huge network form. The dark web uses encrypted transmission, P2P networks, multiple Point relay obfuscation, etc., is a kind of technical means to provide users with anonymous access to Internet information, and its most prominent feature is anonymity. Thanks to GWF, the NB firewall, more than a billion netizens basically can't access the dark web. Of course, even if there is no, ordinary people can't touch it. At least the Great Wall Firewall has given you an extra layer of isolation. China The Internet is relatively safe, and the content is more in line with the core socialist values. The dark web also creates an environment for the application of bitcoin, because anonymous money is more suitable for anonymous people to do anonymous things. One more word, with the development of supervision in various countries, the anonymity of Bitcoin has become much worse, and the truly anonymous digital currencies such as Zerocoin and Monero have begun to be used more widely. Can the dark web be breached? Partially, yes; all, impossible. Whether you accept it or not, it's here to stay for a long time.
Internet technology is no longer something that can not be understood, because there is almost no time when you have nothing to do with it, and in the future, our lives will be entangled with information / Internet technology, you have me and I have you, even artificial The final form of intelligence may be intelligent people . At that time, people are machines and online life. The Internet is no longer a simple network technology, but a cross of various disciplines and branches into multiple fields. This film uses the lens to convey the progress of Internet technology and how this double-edged sword has changed the fate of a group of people. When I watched "The Internet Lost" before, I hoped that more people could see the technological progress through the development of the plot. "Unfriend 2" is better in terms of the amount of information, technical types, and depth, and the shooting method is also more natural. The feeling is stronger, the palms are sweaty after watching, and the armpits are also sweating. .
Finally, I am currently engaged in the SaaS business of trusted computing technology, which is the infrastructure of Web3.0, the next-generation Internet. Trusted computing is a new technology that combines MPC/TEE, blockchain, AI, big data and distributed computing. The first round of equity financing has just been completed. The demo of the personal credit investigation scenario is in progress. The problem of data collaboration on the premise of protecting personal privacy. Although there is still a long way to go from ideal realization, hopefully in the near future, you will also be a beneficiary of the technology we develop.
The above will not go into details.
View more about Unfriended: Dark Web reviews